gdb - writeup
Morten Hansen • July 7, 2021
WRITE-UP
Challenge:
I think the flag might be decrypted and left in memory. Maybe a debugger will help?
Check out the CTF @ ForeverCTF
Steps to do:
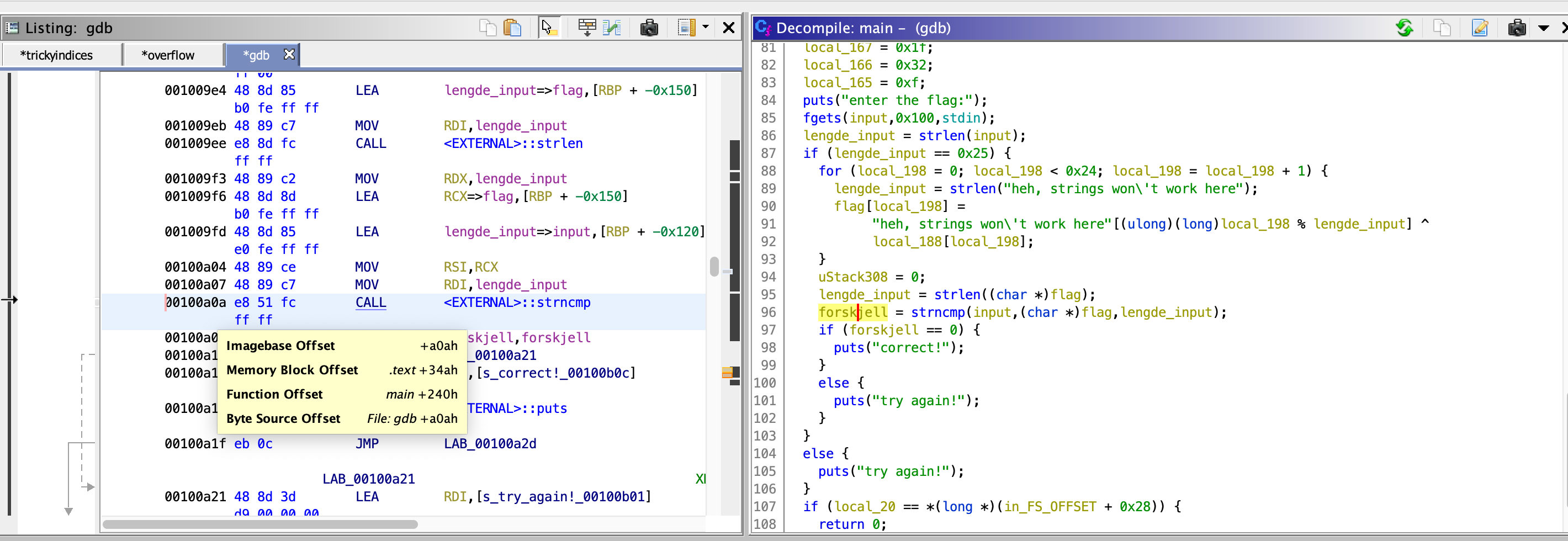
Open file in Ghidra. Change name on the values. Find out what we know for certain.
Run
gdb -q ./gdbin order to debug it.- Start debug-session with
startand mark breakpoint withbreak *main - Type
runto run - We find out from Ghidra that the length have to be 36 bytes (not 37, because of \n appended)
- At what point are we certain that the flag excists in the memory? Hower over the function in Ghidra at that point and note the "Function offset" which in this case is
main +240h. the240hstands forhex 0x240 - open
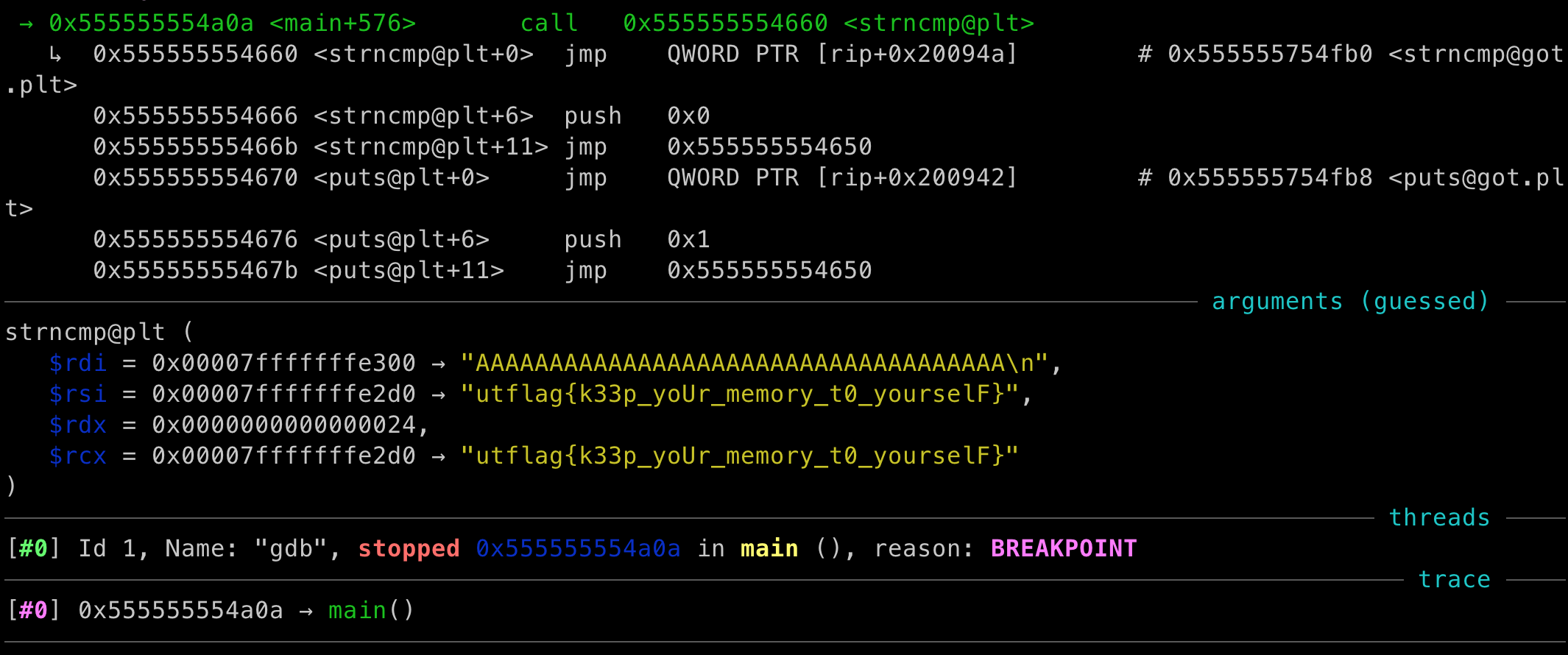
gdbagain, start debug and set breakpoint atbreak *main + 0x240 - Run the file and type in a string with length of 36. Watch the outcome that is the flag
Finish
Thanks to langemyh
